Hyperlane is a permissionless cross-chain interoperability framework that has transformed blockchain security by stopping over $3.5 billion in bridge attacks through its cutting-edge modular security design. Unlike conventional bridges that depend on centralized validator groups, Hyperlane allows developers to implement secure cross-chain messaging on any blockchain network without authorization, with configurable Interchain Security Modules (ISMs) that provide applications full control over their security needs.
Understanding Hyperlane: Comprehensive Guide to Modular Cross-Chain Security
The Hyperlane bridge is an open-source interoperability system built to link different virtual machines (VMs), blockchains, and applications in the blockchain space. The system was developed to address the most pressing issue in cross-chain infrastructure: the structural weaknesses that have resulted in over $3.5 billion in bridge attacks.
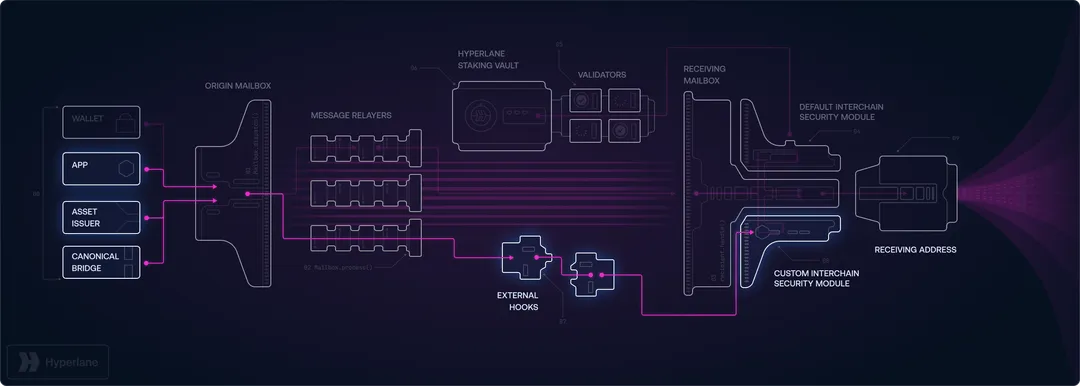
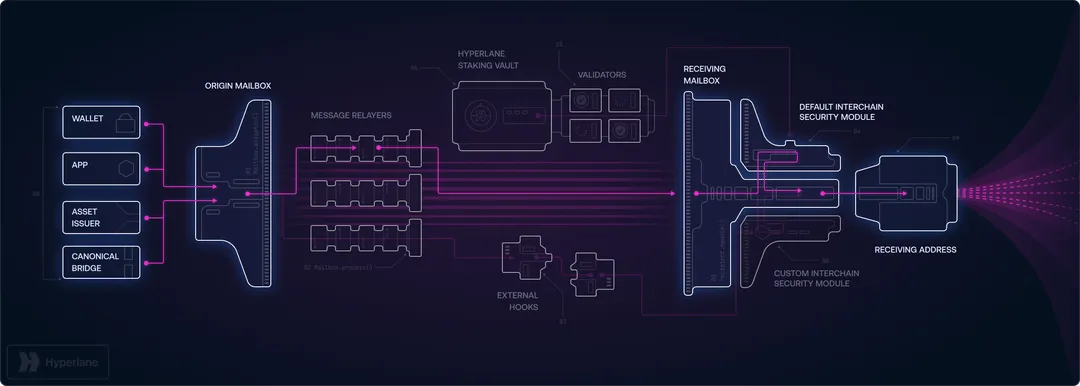
In contrast to traditional bridges that employ single security models with centralized validator groups, Hyperlane uses a permissionless implementation model with modular security. This enables any developer to deploy Hyperlane's Mailbox contract on any blockchain without needing approval, and every application can tailor its security needs through Interchain Security Modules (ISMs).
The hyperlane crypto platform represents a fundamental change in cross-chain security, shifting from centralized, uniform security models to distributed, customizable security frameworks that stop exploits and minimize bridge risk throughout the entire ecosystem.
Hyperlane's Key Innovation: Permissionless Cross-Chain Connectivity
Hyper token enables permissionless deployment of cross-chain messaging infrastructure on any blockchain. Unlike traditional bridges that need centralized approval, Hyperlane's Mailbox contract can be deployed by any developer on any chain, establishing truly decentralized interoperability.
Permissionless Implementation
Any developer can deploy Hyperlane's core messaging infrastructure on any blockchain without needing permission or approval. This removes centralized gatekeepers and establishes a truly decentralized cross-chain ecosystem. Applications maintain full sovereignty over their security parameters and can customize their Interchain Security Modules (ISMs) to align with their specific risk profiles.
Modular Security Framework
Hyperlane's Interchain Security Modules (ISMs) enable applications to select their own security models. High-value transactions can employ conservative, multi-layered security approaches like Multisig ISMs or Aggregation ISMs, while low-value operations can use faster, more cost-effective verification methods like Optimistic ISMs. This modular approach stops exploits by enabling customized security models.
Distributed Failure Domains
Traditional bridges create systemic risk through centralized validator sets. Hyperlane distributes security responsibility across individual applications and chain developers. Any potential compromise remains isolated to specific implementations, preventing the "blast radius" effect that has caused billions in losses across traditional bridge architectures.
The Challenge: $3.5B+ Lost to Bridge Attacks
The blockchain ecosystem has lost over $3.5 billion from bridge attacks as of 2025. Traditional bridges use flawed security models with centralized validator sets that create single points of failure. When validator keys are compromised, entire bridges become vulnerable, leading to massive financial losses.
Why Traditional Bridges Fail:
Traditional bridges suffer from three critical vulnerabilities:
- Centralized Validation Architecture: Single validator sets create systemic risk where compromise of most validators can drain entire bridges
- Monolithic Security Model: One-size-fits-all security creates dangerous "blast radius" effects where one exploit affects all cross-chain assets
- Permissioned Deployment Control: Centralized governance creates bottlenecks and single points of failure that can be exploited or manipulated
Hyperlane solves these problems through permissionless deployment and modular security architecture that prevents exploits and reduces bridge risk across the entire ecosystem.
Interchain Security Modules (ISMs): Customizable Security for Every Application
Interchain Security Modules (ISMs) are Hyperlane's core innovation in cross-chain security. These smart contracts operate on destination chains and verify the legitimacy of incoming cross-chain messages. Unlike traditional bridges that use uniform security models, ISMs let applications customize their security requirements based on specific risk profiles.
- Multisig ISM: Uses a configurable m-of-n threshold signature scheme requiring multiple independent validators to cryptographically attest to message validity. Prevents private key compromise by requiring simultaneous compromise of multiple independent validator keys.
- Aggregation ISM: Uses a composite security model requiring verification from multiple, independent ISMs operating in parallel. This defense-in-depth approach combines different security mechanisms (e.g., Multisig AND Light Client verification) to prevent single security model failure.
- Optimistic ISM: Uses an optimistic verification model with community-monitored fraud windows. Messages are initially accepted and processed, with designated Watchers able to submit cryptographic fraud proofs during a configurable challenge period to revert malicious transactions.
- Rollup Hook ISM: Integrates directly with native rollup security mechanisms, leveraging the underlying blockchain's inherent fraud and validity proof systems. This eliminates redundant security layers by utilizing the rollup's canonical security guarantees.
This modular security architecture is what makes Hyperlane token the preferred choice for secure cross-chain interoperability, preventing exploits through customizable security models that match each application's specific needs.
Why Choose Hyperlane? Key Benefits and Features
Hyperlane docs stands out from other interoperability solutions through several key advantages:
Security and Modularity
- Permissionless Deployment: Deploy cross-chain messaging on any blockchain without requiring approval or permission
- Modular Security: Customize security requirements through Interchain Security Modules (ISMs) that match your application's risk profile
- Decentralized Failure Domains: Security responsibility is distributed across applications, preventing systemic risk from centralized validator sets
- Open Source: Fully auditable codebase with transparent security mechanisms
Performance and Reliability
- Flexible Security Models: Choose security models that balance speed, cost, and security based on your needs
- Economic Safeguards: Verifiable fraud proofs and economic slashing mechanisms align validator incentives with protocol security
- Replay Attack Protection: Globally unique message identifiers prevent double-spending and replay attacks
- Security-Agnostic Relayers: Relayer infrastructure cannot manipulate message content, ensuring security remains in the ISM framework
Economic and Technical Safeguards: Multi-Layered Protection
modular security architecture implements multiple layers of economic and technical safeguards to prevent fraud and malicious attacks. These mechanisms work together to ensure the security and integrity of cross-chain communications.
Key safeguards include:
- Verifiable Fraud Proofs: Designated Watchtowers can submit cryptographically verifiable fraud proofs that trigger automatic slashing of validator staked assets, creating strong economic incentives for honest behavior
- Economic Slashing: Validators must stake substantial collateral, and fraudulent message attestations result in automatic slashing, aligning economic incentives with protocol security
- Replay Attack Protection: The Mailbox contract prevents replay attacks through globally unique message identifiers and complete delivery history mapping, ensuring each message can only be executed once
- Security-Agnostic Relayers: Relayer agents function purely as message delivery mechanisms without security privileges, removing relayers as potential central attack points
permissionless interoperability ensures the security of cross-chain operations through these comprehensive safeguards that prevent exploits and maintain the integrity of the interoperability framework.
The Future of Hyperlane: Building Secure Interoperability
The hyperland team is constantly innovating and expanding the platform's capabilities. Our development focuses on:
Ongoing Innovations
- Additional ISM Types: Expanding the range of Interchain Security Modules to support more use cases and security models
- Enhanced Validator Networks: Growing the decentralized validator ecosystem through partnerships with EigenLayer and other restaking protocols
- Developer Tools: Comprehensive SDKs and documentation to make it easier for developers to integrate Hyperlane
- Cross-Chain Applications: Supporting more applications and use cases across the multichain ecosystem
- Security Research: Continuous security audits and research to identify and prevent new attack vectors
Community and Support
Interchain Security Modules maintains active community engagement through regular updates, transparent communication, and comprehensive documentation. Developers can connect with the team via Discord, GitHub, and Twitter for assistance with integration and security questions.
Hyperlane vs. Other Bridges: Why We're Different
While several platforms offer cross-chain bridging services, blockchain interoperability solutions distinguish themselves through unique advantages:
Permissionless Deployment
Unlike competitors who require centralized approval, modular security systems enable permissionless deployment of cross-chain messaging on any blockchain, creating truly decentralized interoperability.
Modular Security Architecture
Our ISM framework allows applications to customize security requirements, preventing the "blast radius" effect that has caused billions in losses across traditional monolithic bridge designs.
Decentralized Failure Domains
xyz signs distributes security responsibility across applications rather than relying on centralized validator sets, preventing systemic risk and reducing bridge exploits.
Getting Started with Hyperlane: Building Secure Cross-Chain Applications
Ready to build secure cross-chain applications? Here's how to get started with Hyperlane:
For Developers: Deploy Hyperlane's Mailbox contract on your chain, configure your Interchain Security Modules (ISMs) based on your security requirements, and start sending cross-chain messages. The permissionless architecture means no approval is needed.
For Applications: Integrate Hyperlane's SDK into your application, choose the appropriate ISM for your use case (Multisig for high-value transactions, Optimistic for low-value operations), and begin secure cross-chain communication.
For Validators: Join Hyperlane's decentralized validator network by staking collateral and running validator nodes. Earn rewards while helping secure the cross-chain ecosystem.
Security Best Practices for Hyperlane Developers
While hyper network xyz implements multiple security layers, developers should follow these best practices:
- Always verify you're using the official Hyperlane contracts from the verified GitHub repository
- Choose appropriate ISMs based on your application's value and risk profile
- Conduct thorough security audits before deploying production applications
- Monitor validator sets and ensure sufficient decentralization
- Implement proper error handling and fraud proof mechanisms
- Stay updated with Hyperlane security announcements and best practices
Conclusion: Why Hyperlane is the Ultimate Cross-Chain Security Solution
hyperliquid block explorer has established itself as the definitive platform for secure cross-chain interoperability. With revolutionary permissionless deployment, modular security architecture, and unwavering commitment to preventing bridge exploits, Hyperlane represents the future of secure multichain communication.
Whether you're building cross-chain applications, deploying on new blockchains, or securing high-value transactions, Hyperlane provides the most flexible, secure, and decentralized solution available today. The modular ISM framework allows you to customize security to match your needs while preventing the systemic vulnerabilities that have plagued traditional bridges.
Join the growing ecosystem of developers and applications that trust Hyperlane for their cross-chain infrastructure needs. Experience the next generation of interoperability with permissionless deployment, modular security, and protection against $3.5B+ in bridge exploits.